Integrate Data, Build Cybersecurity Roadmaps
Integrate existing company data quickly from Excel, Visio, SharePoint etc
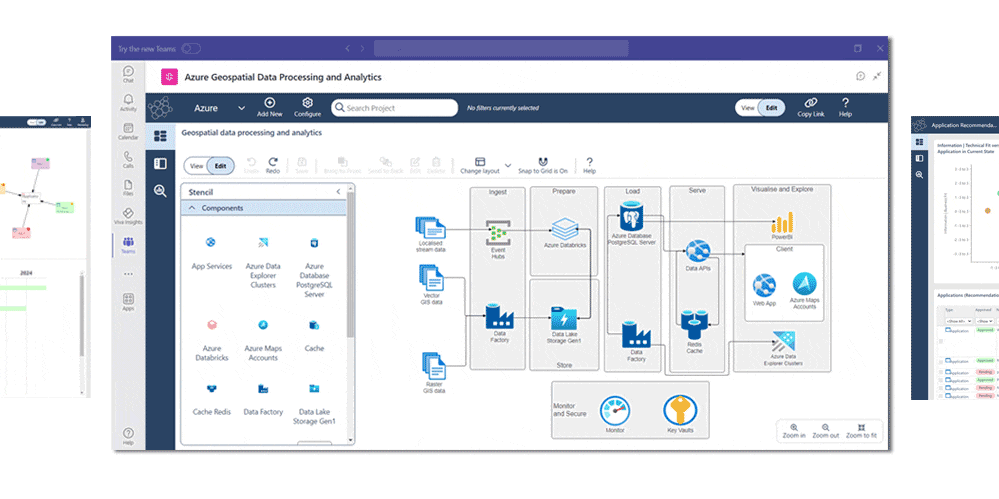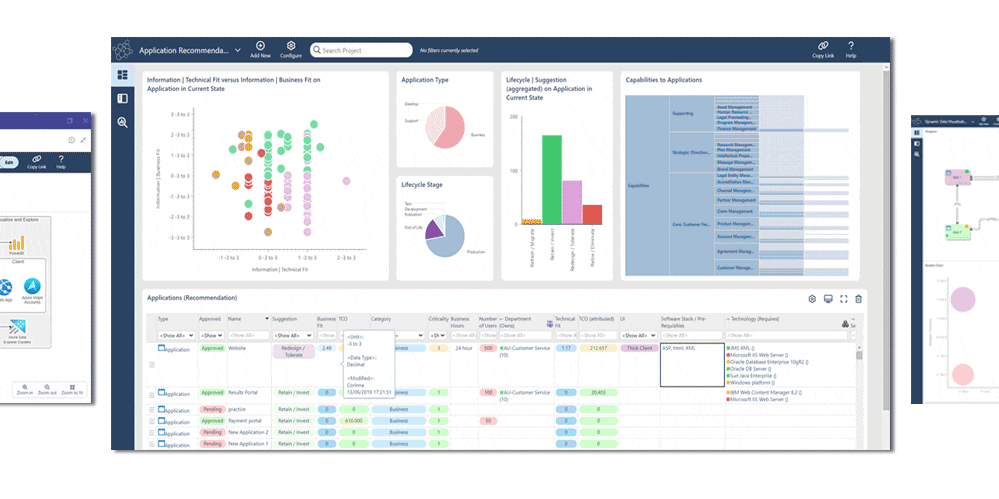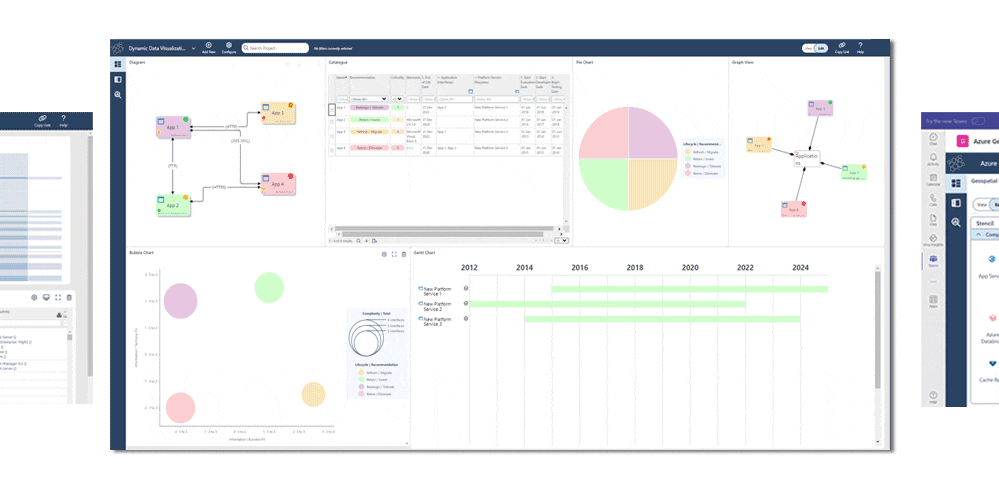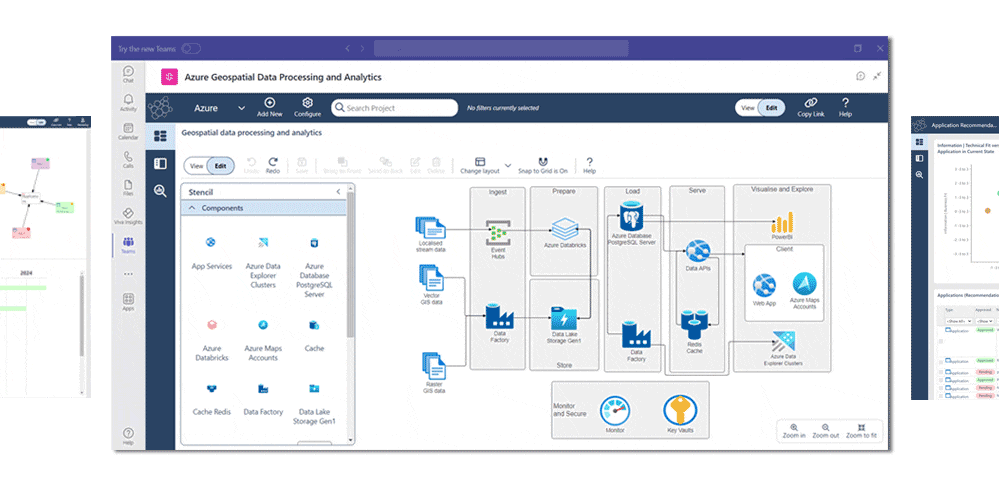
- Model systems, technology and infrastructure. Set up Application Catalogs, Application Landscapes and Business Capability Maps
- Use frameworks and standards to accelerate your strategies. Options in ABACUS include TOGAF, ArchiMate, BPMN, specialised security frameworks NIST , Essential Eight and SABSA and cloud architecture libraries such as AWS and Azure
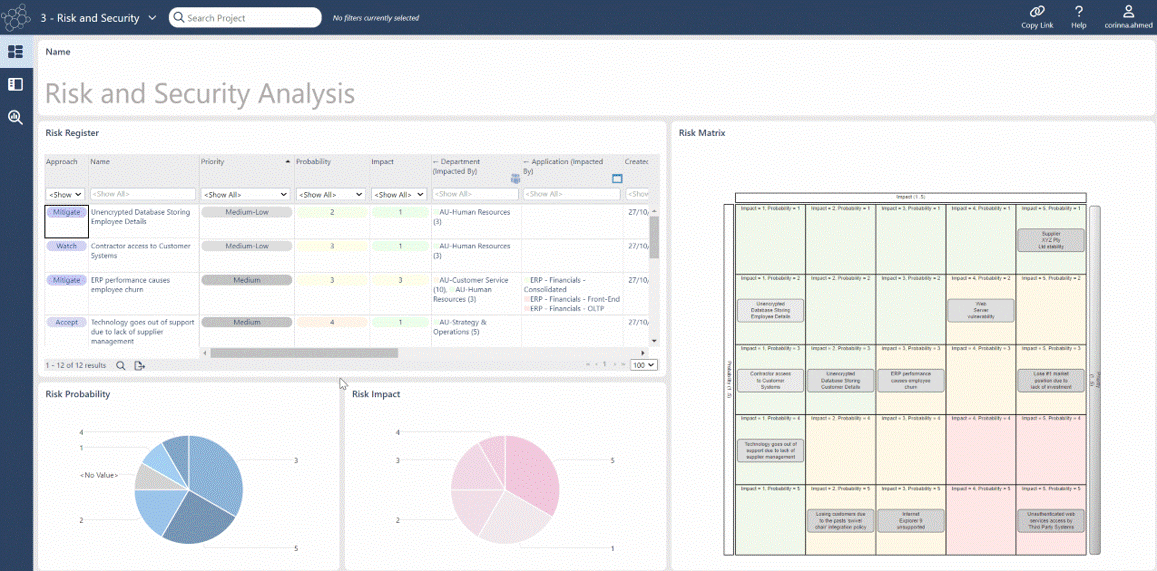
- Rate applications and infrastructure risk to identify priorities. Run Security Risk Scoring: a function of the probability and impact of attack
- Analyze scenarios and present metrics: quantify Risk, Security, Performance, Reliability, Resource Utilization, Response Time
Enterprise Architecture for Cybersecurity
Set up self-service data management for data-owners with editable browser-based lists and diagrams. Set permissions which allow teams across your organization to access and update data.
- Use permissions and SSO to ensure Confidentiality, Integrity, and Availability of your information
- Assemble cybersecurity dashboards to provide at-a-glance reports including risk matrices, cost- calculations and Gantt charts to track projects
- Use graph-database analytics to understand cybersecurity dependencies and impacts
Cybersecurity Strategies
How can enterprises build agility to detect and respond to the unknown and unexpected?
Living in an digital world creates both new opportunities but also new risks and increased regulatory requirements.
Architects can use connected data and models in ABACUS to design resilient systems, identify security vulnerabilities and developed informed risk mitigation strategies.
Download our cybersecurity eBook to uncover the secrets and trends into turning your enterprise architecture into your digital safeguard.
An Enterprise Architect’s Guide to NIST for Cybersecurity
Cybersecurity is a top priority for many organizations. More than 85% of organizations are looking to increase their IT security spending, according to McKinsey.
Watch our 5-min guide for an overview of the popular NIST cybersecurity framework. Used widely in the US, NIST CSF provides industry standards and best practices to help organizations manage risk and cybersecurity.
“Our team are using ABACUS as one of their guiding lights to prioritize cybersecurity”
Scott Frederick – Infrastructure Architect, Ameritas


