Guide to Strategies for Mitigating Cybersecurity Incidents
Threats to an organization’s cybersecurity present one of the chief challenges for modern enterprises. Cybersecurity attacks on Australian businesses more than doubled between the 2019-20 and 2021-22 financial years, as reported by the Australian Bureau of Statistics.
An important element of cyber defences is a robust enterprise architecture, and cybersecurity frameworks, providing a scaffold for successful security practices. The Essential Eight cybersecurity framework stands out for its targeted technical controls. It offers three distinct maturity levels, providing enterprises with a clear roadmap towards progressively stronger defences.
What is the Essential Eight Framework?
Developed by the Australian Signals Directorate – an Australian federal government agency – the Essential Eight is a cybersecurity framework that sets out to assist organizations in protecting themselves against cyber threats.
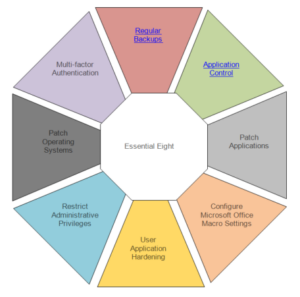
The framework outlines a series of mitigation strategies and principles designed to safeguard Microsoft Windows-based internet-connected networks. The strategies detail a minimum set of preventative measures required to achieve adequate protection.
The eight controls identified are designed to complement each other, with organizations recommended master a maturity level before progressing onto the next.
Essential Eight and Other Cybersecurity Frameworks
The Essential Eight’s streamlined approach provides an accessible starting point to cybersecurity in comparison to other frameworks, such as the NIST Cybersecurity Framework (from the US National Institute of Standards Technology). While NIST features 108 Mitigation Strategy Categories and 1,177 Security Controls, the Essential Eight framework lists 8 Categories and 69 Controls.
With targeted security controls, focused preventative measures and condensed mitigation strategies, the Essential Eight offers an easier entry point for organizations.
Implementing Essential Eight with Your Enterprise Architecture
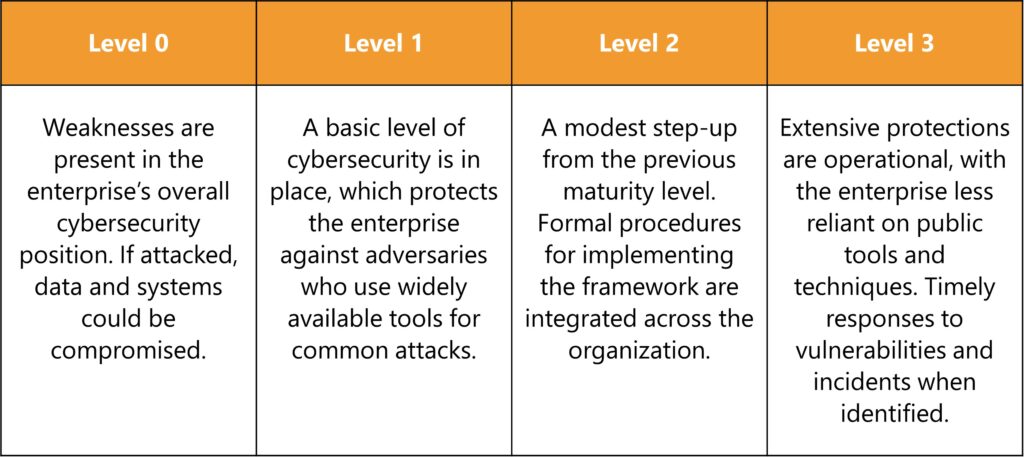
The Essential Eight offers a staged approach to incorporating cybersecurity across an organization, allowing enterprises to steadily ramp up their defences. The framework defines four maturity levels, ranked from zero to three. These levels are aimed at progressively assessing, monitoring, and improving the framework’s application.
How can an enterprise architecture team apply the framework?
- Identify your cybersecurity maturity level
- An organization’s maturity level considers the likelihood of being targeted and the consequences of a cyber-attack. Higher levels feature additional measures and controls.
- Incorporate the Essential Eight into the organization’s existing metamodel
- Once a maturity level has been chosen, the corresponding list of mitigation strategies and preventive measures can be incorporated into existing metamodels, similarly to how generic business strategies and processes are modelled.
- Develop a cybersecurity compliance profile
- Once a compliance profile is built, a scoring algorithm, which in nature awards compliance and punishes non-compliance, can be created to provide a visualized metric.
- Compliance metrics can be measured over time, with changes in architectural activities being monitored. Future state planning and gap analysis can be implemented to provide an actionable roadmap for organisations to build robust cybersecurity practices within EA functions.
Modeling Essential Eight with the ABACUS Enterprise Architecture Software
Using an architecture modeling tool such as ABACUS to implement your cybersecurity framework provides a more holistic and connected view of your security position. ABACUS provides a comprehensive store of enterprise architecture, security architecture and business processes. Your teams’ ability to diagnose vulnerabilities, track implementation progress and streamline framework adoption is well supported. This includes
- Boosting compliance with closer monitoring of framework implementation. Granular level visibility empowers teams to address compliance gaps and remain on track across domains.
- Applying a high-level enterprise architecture approach to risk management means your team can:
- Model future-state architectural cost/benefit analysis to determine risk acceptance/residual risk levels.
- Conduct process and business capability modeling for organizational adoption of security practices.
- Perform gap analysis of current/target state to plan for transition roadmap.
- Set up analytics to automate and monitor progress on your security and risk scores.
- Generate scripts for automatic diagram creation. Perform impact analysis with World According To diagrams.
- Machine learning assists by auto-filling gaps in your data with predictions based on existing patterns.
- Collaborative dashboards engage stakeholders from across the organization to track and allocate cybersecurity activities.
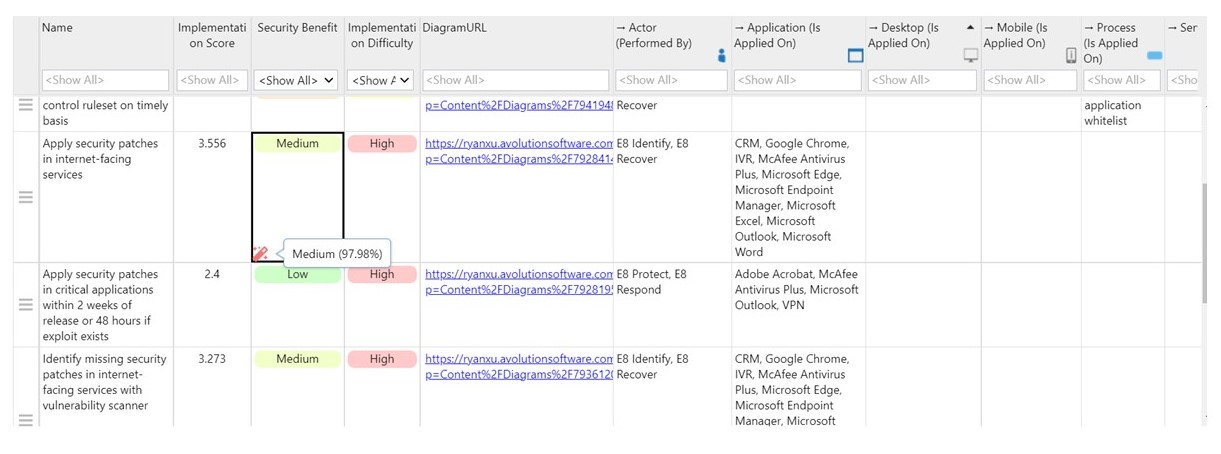
Essential Eight catalog in ABACUS

