Managing sensitive data well ensures organizations can:
- Gain visibility of, and be proactive about data flows and data-management
- Ensure integrity of datasets and insights
- Minimise risk of fines or sanctions
- Protect corporate security and reputation
- Enable the flow of anonymized key data as a resource

Legislation governing data management globally includes:
- General Data Protection Regulation (GDPR EU, in force May 2018) governs protection of EU citizens’ data
- California Consumer Privacy Act (CCPA United States, in force 2020). Covers privacy rights, and transparency in how data is collected, shared and used
- Protection of Personal Information ACT (POPI South Africa, in force 2018) requires organisations to exercise proper care when collecting, storing or sharing personal data
- Prudential Standard CPS 234 Information Security (Australia, in force 2019) defines information security controls for information assets in financial services
DOWNLOAD EBOOK: An Enterprise Architect’s Guide to Data Privacy and Security
“You’ve got to show you have control of data governance, both as a company operating in the finance sector, and when handling personal data under GDPR. In ABACUS, we can identify the systems with sensitive personal information.”
Chief Architect (Financial Services)
Read how this architecture team streamline compliance and strategic planning
Build A Data Management Strategy to Protect Privacy and Personal Data Records
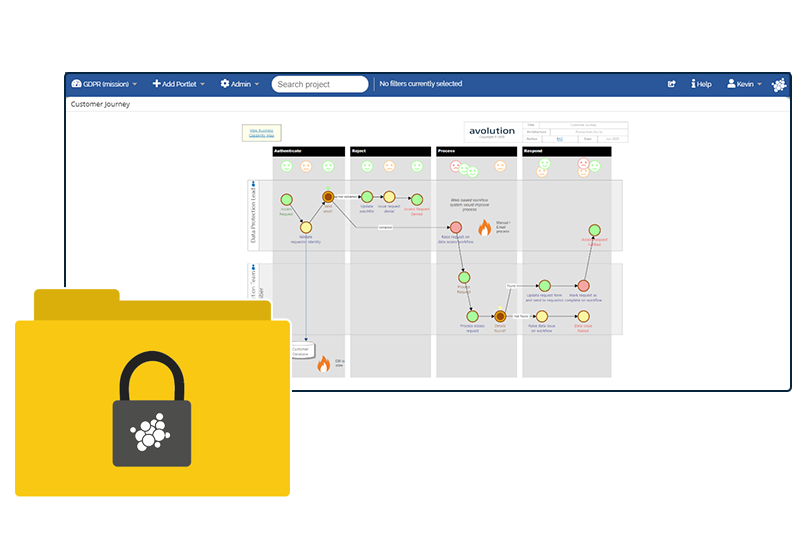
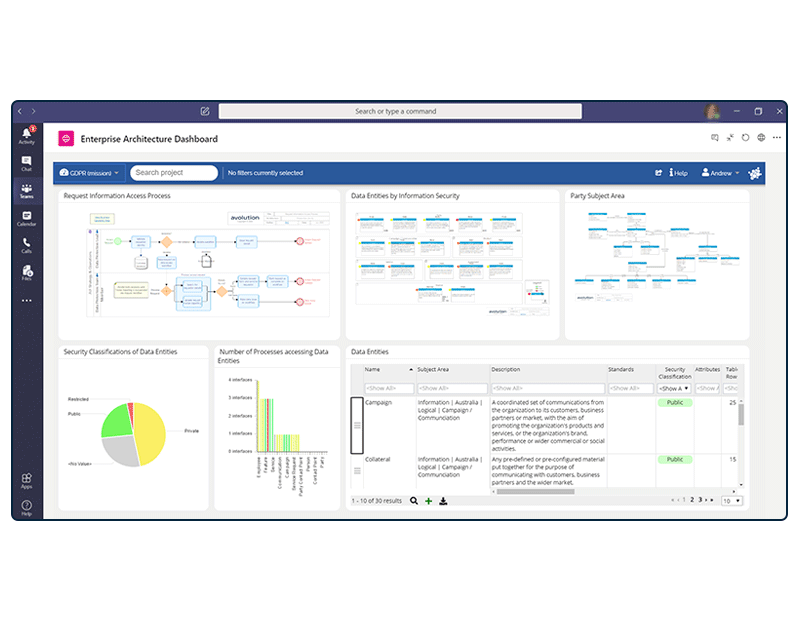
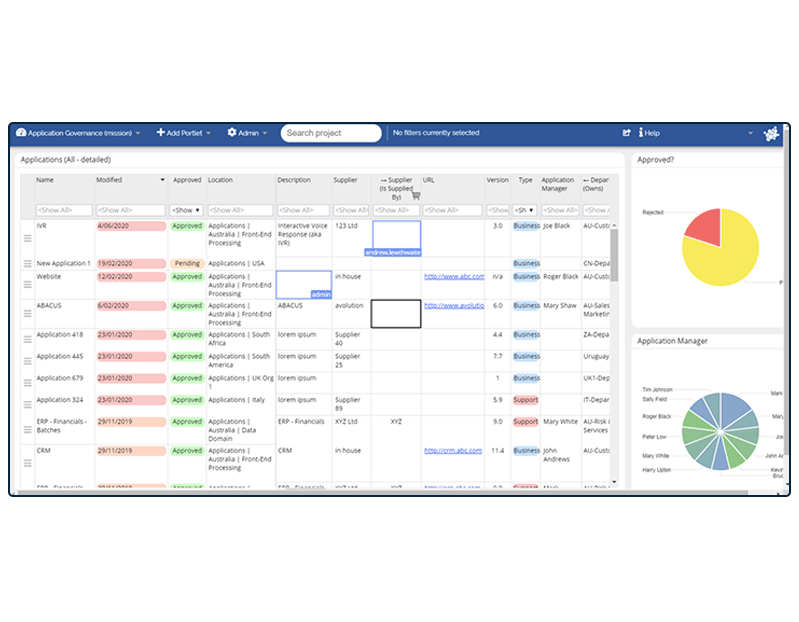
ABACUS supports data privacy compliance by providing the data management environment needed to centralize and model and analyze data:
- Audit information: connect the tools your organization uses via APIs, build integrations with SharePoint, databases and CMDBs, and leverage existing EA catalogs using Excel roundtripping, to speed this process. Ensure users business-wide can update changes easily using collaborative data management.
- Model interdependencies and data flows: including process, information and technology interdependencies. Be guided by frameworks to develop an interconnected map of the company’s systems, applications, business capabilities and processes, and how they support departments and critical projects
- Prioritize data by risk and value: taking into account sensitivity, volume and type of data and any known security vulnerabilities. Set up algorithms to keep your risk-scoring current.
- Discover Shadow IT: Use algorithms in ABACUS to make inferences about the existence of Shadow IT data (unauthorized and “invisible” data).
- Report: Set up interactive dashboards and automate compliance reports. Use charts, heatmaps, matrices and flowcharts to explain current and future states: impact of compliance violations, costs of compliance and the financial risks of non-compliance
- Roadmaps for strong compliance and innovation: build an enterprise architecture roadmap for any remediation or updates required. Set these to update as projects progress.
ABACUS also provides strong functionality for enterprise architects managing and modeling cybersecurity risks and threats.
Enhance Your Data Privacy Solution With ABACUS
Discover how ABACUS can help your enterprise reduce risk and threats with our series of resources

Webinar



